
Binary Armor Virtual Guard
Binary Armor virtual guard solution is a device-independent software implementation of Binary Armor
Binary Armor virtual guard is ideal for OEMs that desire best-of-breed cybersecurity capabilities hosted on their own control systems or network devices. Binary Armor virtual guard delivers the same trusted and proven technology that powers the SCADA network guard in a virtualized environment, enabling extreme flexibility and protection for a broad range of devices.
The applications of Binary Armor virtual guard is seemingly endless, from servers and switches to wireless access points, radios, PLCs, RTUs and IoT control units. Let us know how we can partner with you to conquer your cybersecurity challenges.
$1.00
- Use Cases
- Documentation
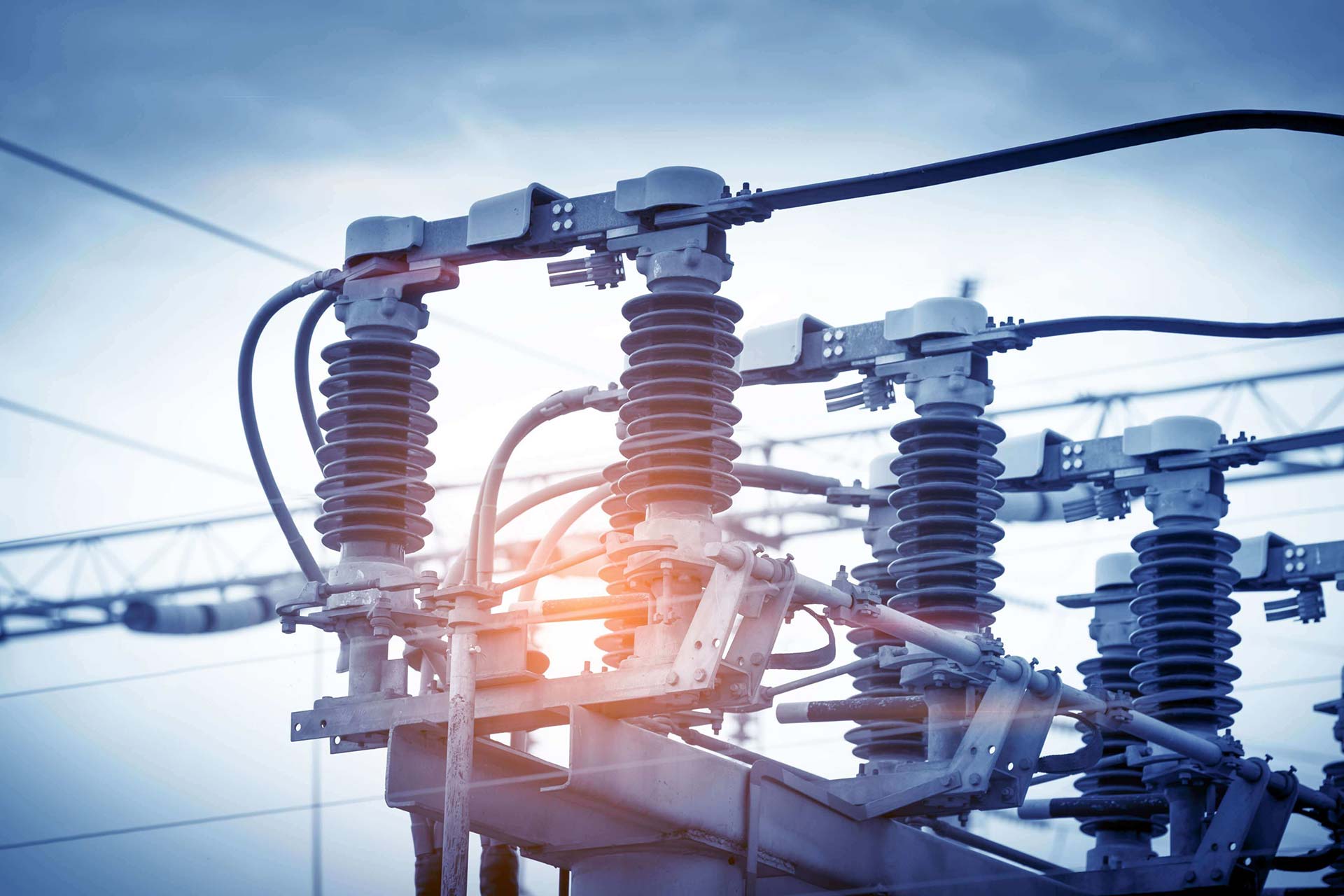
Binary Armor virtual guard can be hosted on an intelligent-recloser’s main processor board. Once integrated, Binary Armor validates bi-directional data traffic using patented state-based processing to ensure no cyber-initiated malicious communications are allowed to trip reclosers and cause grid-wide outages.

Binary Armor virtual guard can be hosted on wireless devices that communicate with automated pipeline valves. Malicious commands attempting to pass through the wireless device and drive unsafe pipeline pressure are stopped cold by the Binary Armor’s enforcement of safe parameters in pressure control messages.

Protected ECDIS are crucial to safe maritime navigation and effective world commerce. Binary Armor virtual guard protects ECDIS for fleet owners and ships captains, restoring the balance in favor of safe navigation throughout the world’s oceans.

Binary Armor virtual guard can be hosted on control station processors to shield PLCs from commands that could release untreated waste-water. By validating and allowing only approved message content, Binary Armor secures water systems against unauthorized changes while two-factor authentication protects against insider threats.

Hosting Binary Armor virtual guard onto Advanced Metering Infrastructure wireless communication devices provides valuable network insight and cybersecurity protection. The Binary Armor’s patented data inspection and blocking functions ensure that flawed or malicious data is not delivered into an electrical utility’s core network where it can wreak havoc.

Internet-connected Building Automation Systems (BAS), while useful for remote energy management, increase building sub-systems’ vulnerability to cyberattacks. Binary Armor virtual guard hosted on a BAS Controller permits only pre-approved data exchange, thus making a malicious code attacks against the BAS network much less likely.
